Resources for the global digital safety training community.
Activity & Discussion: Software Treasure Hunt
Credits Last Updated 2016-05
In this Activity, participants take a close look at the software on their computer and answer key questions regarding each application’s safety and status. This then leads into a Discussion about key habits for safer management of existing software, and for downloading new software.
ADIDS Element
Activity and DiscussionParent Topic(s)
Safer Software UpdatingDuration
30-45 minutesMaterials to Prepare
- Treasure Hunt “Matrix” (see below) on large paper or projected onto a wall.
- Matrix should include the latest version number available for each of the most common applications that the participants use. Some titles are suggested below.
- Laptop (and projector if projecting matrix)
Running the Activity
This activity will highlight the differences in software versions for each participant’s computer. At the end, the discussion will focus on teasing out current practices (or lack thereof) for keeping software up to date, and then lead into the Input section where best practices will be presented.
When making the matrix, leave enough space to fit everyone’s version number in as they share them out.
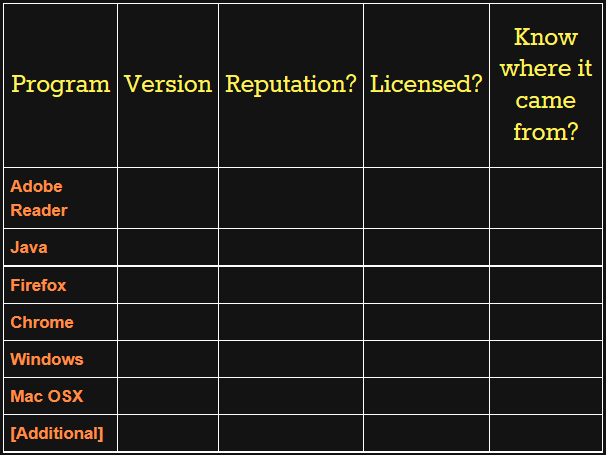
Step 1: Common Applications
Ask participants to try to find the version number of the applications that you have listed in the left-hand column of the matrix.
- Some participants will be able to find version numbers, but others will need direction. If they are running Windows, you can instruct them to open ‘Add or remove software’ from Windows Control Panel or to open the program and find the version number under the “Help” or “About” menu.
- Have participants call out their version numbers one at a time.
- Leave the operating system for last. Ask participants to open Windows Update and find the date of last update. Add that to the matrix.
Step 2: Suspicious Applications
- Ask participants to open Add or Remove Software (Control Panel->Programs->Programs and Features).
- Ask participants to examine it for software they don’t recognize or that have suspicious names (e.g. “SuperSpam-u-lator”).
- Add those programs to the matrix in the far-left “Program” column.
- Make a notation in the corresponding “Reputation?” box in the third column.
Step 3: Pirated Applications
- Ask participants if any of them know of a pirated application they have installed on their PC (remind them you’re not the Software Police!).
- Provide some popular examples - good ones include Photoshop, Microsoft Office Suite programs, NitroPDF, and Adobe Acrobat. Add these new programs to the left-hand “Program” column.
- Make a notation in the corresponding “Licensed?” box in the fourth column.
Step 4: Filling out the Matrix
Looking through the list once again, ask the group to help complete the matrix. Ask where people got all their software? As you review individual applications, use these guidelines:
In cases where the application is FLOSS** (Free/Libre open source software)
- Mark ‘free/open source’ in the License? Column.
In cases of suspicious software,** ask the group what they think:
- Who uses the application?
- What was the source for the application?
Leading the Discussion
Highlight the differences in version numbers, and point out examples where participants have out-of-date software.
Ask participants to share their habits related to software updates:
- Do they allow automatic Windows updates?
- Do they skip or put off automatic updates? If so, why? (Are they concerned their PC will stop working?)
- Do they assume all other software is updating itself automatically?