Resources for the global digital safety training community.
Organizational Security Plans and Protocols
Credits Last Updated 2017-06
In this session, you will facilitate a process for women to develop a security plan and corresponding protocols that they can use to implement digital security measures in their own organization.
ADIDS Element
DeepeningParent Topic(s)
Security Plans and ProtocolsDuration
90 minutesThis session was developed for, and should be attributed to, the Institute for War & Peace Reporting resource “Cyberwomen: Holistic Digital Security Training Curriculum for Women Human Rights Defenders” under a Creative Commons Attribution-Share Alike 4.0 International CC BY-SA 4.0 License
Materials to Prepare:
- Risk model from Deepening session Gender-Based Risk Model
- Printed security protocol templates (see example template below)
Trainer’s Note
- This session is best suited for participant groups who come from the same organization or collective, as the activities below are focused on developing an organizational level security plan – the process of designing this together will help support women’s ongoing practice and implementation of it.
- It is crucial to follow-up with participants on the implementation of the plan they create – if possible, connect with them every two or three weeks to check on progress (apart from answering any questions they might send in the interim). Be careful not to pressure participants about using specific tools or implementations of them when follow up with them – simply support them and be present with them, responding to any questions or concerns they have and providing recommendations when requested. If participants feel pressured, they may not be forthcoming about whether they’ve addressed a specific issue and won’t feel comfortable sharing actual difficulties when they arise.
Running the Session:
Part 1 – Return of the Risk Model
Step 1 | Begin the session by highlighting the importance of building a risk model before drafting a plan and any protocols. Remind participants that digital security is first and foremost a personal process - if their goal is to draft and implement a digital security plan at an organizational level, explain that it will be a process of:
- Mapping threats collectively - this can be done over the course of a couple training sessions with the entire team present, however remind the group that remaining aware of and updated on the threats they face will be an ongoing process.
- Learning the difference between strong habits and unsafe habits of digital security, and remaining up to date on new tools or updates to existing ones.
- Making implementation decisions together as a team, but also identifying areas where individuals can create and practice their own processes as they see fit.
- Consistently monitoring the implementation of their organizational digital security plan, ensuring that corresponding protocols are well understood before they are practiced, and troubleshooting any emerging difficulties throughout.
Part 2 – Plans vs. Protocols
Step 2 | Explain to participants the difference between a digital security plan and a digital security protocol. The main idea to communicate is that:
- A plan is an outline of key changes that an organization or collective has identified as requirements for increasing their digital security. Plans are a defined process, with a beginning and an end.
- A protocol is a set of measures or actions related to digital security that are each connected to a specific activity or process within an organization or collective. Protocols are ongoing practices that remain in effect even when a digital security plan has been fully implemented, and will evolve over time in response to changes in risk and threat environments.
Provide examples of plans and protocols to participants – for instance, activities such as travel or participation in public protests would each have their own digital security protocol; items found in a digital security plan might include an organization having their website audited, verifying that every computer has antivirus installed, and introducing the use of GPG to encrypt emails.
Part 3 – Creating an Organizational Plan and Protocol
Step 3 | This session is best suited for participant groups who come from the same organization or collective, as they can take advantage of this opportunity to collaborative develop their plan and protocols as a team. However, if this is the case for only some participants, those who are not part of any organization or group can still participate in the session by working on their own personal plans and protocols.
Step 4 | Ask participants to refer to their risk model from the Deepening session Gender-Based Risk Model. Have them begin making a draft of their security plan - the following format may be useful:
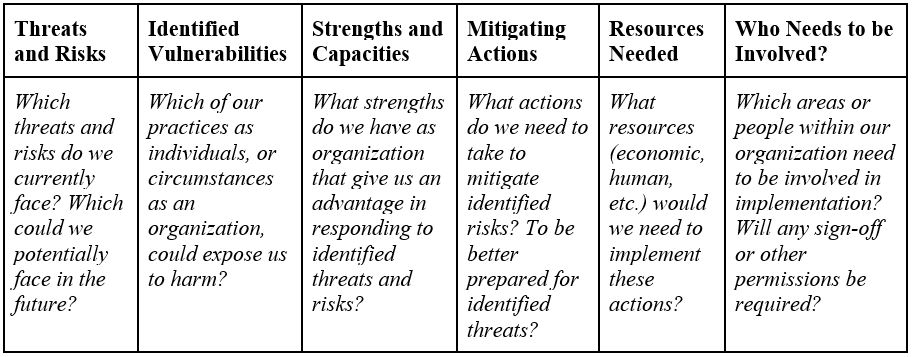
Explain to participants each of the sections - a new row should be started for each risk or threat identified.
Step 5 | Remind participants that although the focus of this training is on digital security, we must always remember to take holistic measures into account. Ask participants to consider which actions need to be taken in terms of physical security and self-care as they draft their security plans and protocols.
Step 6 | Then, after participants have finished their first draft of the plan template, ask them to then build a list of their organization’s activities or processes that they feel will require individual protocols.
Step 7 | Once participants have finished both their draft plan template and their list of activities requiring security protocols, it will be useful to pause so that everyone can share their plans. This presents a valuable opportunity for participants to learn from the approaches of others; however, remember that some may not feel comfortable sharing their organizational or personal vulnerabilities as a matter of trust. To address this proactively, you may want to ask the group to share only the key items for their plan (the 4th column of the template table, “Mitigating Actions”) while keeping other information like “Threats and Risks” and “Identified Vulnerabilities” private.
Part 4 - What’s Next?
Step 8 | Discuss follow-up steps with participants - they will need to have a focused gathering within their organizations to share insights and key takeaways from this session, as well as the Deepening session Gender-Based Risk Model – of special importance from this session will be the list of activities and processes requiring security protocols. This plan will need to be discussed and agreed upon as a team, with realistic dates set for its implementation – while considering these, participants also need to remember that there may be others in their organizations who will require training on digital security practices and/or specific tools for full implementation to be possible.